Migrating data or systems is a complex endeavor, fraught with potential pitfalls if not managed properly. We understand the critical importance of a meticulous approach to transitioning crucial information from one environment to another. A migration checklist template is an indispensable tool for orchestrating a smooth and secure transfer process. It serves as a strategic guide through the planning, execution, and post-migration phases, ensuring nothing is overlooked and all goals are met methodically. A comprehensive plan tailored to the project’s specific needs, refined through a detailed data migration strategy, is vital for success.
Creating a migration checklist involves comprehensive pre-migration planning. This anticipates the technical requirements and identifies potential risks and mitigations. Budgeting and cost analysis are also integral to this phase, establishing a financial framework that aligns with the project’s objectives. When we develop our migration strategy, its execution must be stringent, incorporating robust security measures to protect data integrity and privacy. Finally, continuous monitoring and optimization post-migration ensure the project meets long-term performance and usability standards, adjusting as needed for the best outcomes.
Key Takeaways
- A migration checklist template frames a strategic approach to data and system transfers.
- Including details on pre-migration to post-migration stages ensures thorough preparation.
- Ongoing assessment post-migration optimizes system functionality and data integrity.
Pre-Migration Planning

Before embarking on a migration journey, it is crucial for us to comprehensively evaluate our current systems and establish clear objectives. Our approach must encompass a thorough assessment of our infrastructure, setting migration goals, establishing a project delivery structure, and identifying the key teams and stakeholders involved in the process.
Assessment of Current Infrastructure
Infrastructure assessment forms the foundation of our pre-migration planning phase. We are tasked with reviewing our current workloads, dependencies, and the overall data quality and integrity of our systems. This involves:
- Cataloging our existing infrastructure components
- Conducting a pre-migration impact assessment to determine how each piece will be affected
- Evaluating the state of our legacy systems to identify potential risks
Defining Migration Goals
For defining migration goals, it is imperative that we establish what we aim to achieve with this migration. Our goals are specific and might include:
- Enhancing performance and scalability
- Improving data governance protocols
- Achieving cost optimization
Project Delivery Structure Setup
Setting up a project delivery structure provides us with a clear framework for the migration process. This encompasses:
- Determining the governance model to guide decision-making
- Creating a comprehensive plan that outlines each stage of the migration
- Envisioning a structure that supports both phased and agile delivery methods
Identifying Technical Teams and Stakeholders
Technical teams and stakeholders are critical to the migration’s success. Our responsibilities include:
- Mapping out all the data stakeholders and their roles in the migration
- Forming technical teams with clear responsibilities and tasks
- Ensuring access to training documentation to equip all parties with the necessary knowledge
Budgeting and Cost Analysis

When we embark on a data migration project, an accurate budgeting and cost analysis is crucial for its success. We must thoroughly understand the financial implications, from calculating the total cost of ownership to identifying any hidden costs and developing strategies for cost optimization.
Calculating Total Cost of Ownership
The Total Cost of Ownership (TCO) for a migration project encompasses more than just the upfront costs. It includes ongoing operating expenses such as maintenance, support, and future upgrades. When we calculate TCO for cloud migration, for instance, we consider both initial migration expenses and long-term costs such as cloud service fees. We emphasize the need for a full accounting to address all potential expenses.
Example TCO Calculation:
- Initial Migration Cost: $50,000
- Yearly Cloud Hosting Fee: $10,000
- Maintenance and Support: $5,000/year
- Anticipated Upgrades: $3,000/year
- Total 5-Year Cost: $130,000
Hidden Costs Identification
Identifying hidden costs is vital to prevent budget overruns. These can include costs associated with downtime during the migration, training staff on new systems, and potential compliance-related expenses. For a full migration, it’s imperative to factor in the possibility of extended timelines affecting the budget due to unforeseen technical or regulatory challenges.
Hidden Cost Areas:
- Downtime and business interruption
- Compliance and regulatory adjustments
- Training for new systems or processes
Cost Optimization Strategies
Cost optimization is an ongoing process starting from the initial budgeting phase through the life of the migration project. We must regularly review our expenses, renegotiating contracts where possible and leveraging cloud cost management tools as part of our cost optimization strategies. Our aim is always to balance the budget without compromising the quality of the migration or the performance of the new system.
Cost Optimization Checklist:
- Regular expense audits
- Contract renegotiations
- Adopting cloud cost management tools
- Streamlining operations to reduce expenses
Migration Strategy Development
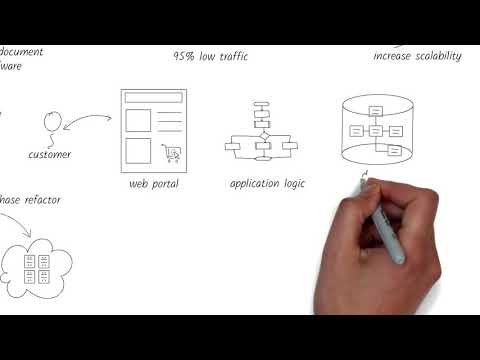
When undertaking the significant task of data migration, we must carefully develop a strategy that addresses key factors such as choosing the right cloud service provider, ensuring data security and compliance, and meticulously planning the migration phases.
Choosing a Cloud Service Provider
In selecting a cloud service provider, we consider the cloud environment that best suits our project’s needs. We analyze providers like Microsoft Azure and AWS, both offering comprehensive Cloud Adoption Frameworks which guide through public cloud adoption. Key criteria include scalability, cost-effectiveness, and alignment with our data migration strategy.
Data Security and Compliance Considerations
Data security is paramount in our migration strategy. We must outline protocols for preventing data loss and ensure our approach aligns with compliance regulations. Our data security plan considers how to best protect sensitive data within the cloud environment and during transit. We incorporate strict security measures and regular audits to adhere to compliance standards.
Migration Phases Planning
Our migration planning involves defining clear migration phases. The initial stage involves creating an inventory and categorizing data for migration. Next, we plan the actual transition, followed by a meticulous verification process in the new environment. Throughout each phase, we must consider potential risks and have contingency plans for data loss prevention.
Technical Preparation

In mitigating risks during data center or cloud adoption migrations, addressing our IT infrastructure robustness, data safeguarding, and network adequacy is imperative.
Upgrading Legacy Systems
We must assess and update our legacy systems to ensure compatibility with new technologies. This involves evaluating the storage capacity and infrastructure performance to determine if they meet the requirements of the migration. Upgrading often includes patching software, replacing outdated hardware, and considering cloud adoption for improved availability and scalability.
- Infrastructure: Replace or update hardware to support newer technologies.
- Legacy System: Patch software to the latest versions where possible.
Ensuring Data Backup and Recovery
A foolproof data backup and recovery strategy is central to our technical preparation. We must ensure that:
- Data Backup: All critical data is replicated in a secure location.
- Recovery: Systems are in place for quick restoration in case of data loss.
Availability of data post-migration is preserved through rigorous backup checks and contingency plans, safeguarding against data disasters.
Network Capacity Planning
Our network capacity needs precise planning to handle increased loads during and after the migration. We must evaluate current network resources to avoid bottlenecks that could impact performance. Planning includes:
- Ensuring sufficient bandwidth for seamless data transfer.
- Storage: Provisioning adequate storage for the migration process.
Our network capacity assessments ensure that data center migration processes do not compromise system performance or availability.
Execution of Migration
In executing a migration, our primary focus rests on transferring data seamlessly, relocating servers and workloads effectively, and ensuring post-migration performance meets or exceeds expectations.
Conducting Data Transfer
We meticulously plan the data transfer process to minimize downtime and ensure integrity. The following steps are taken:
- Preparation: We inventory all data sets and categorize them according to sensitivity and size.
- Transfer: Utilizing robust transfer protocols, we move data to the new environment.
- Verification: Post-transfer, we compare source and destination data for consistency.
This phase is crucial for the continuity of business operations and maintaining data integrity.
Server and Workload Migration
Our server migration is designed to ensure scalability and adaptability. Here’s how we manage the deployment:
- Assessment: We evaluate our servers to ascertain migration readiness.
- Strategy: A tailored migration plan, specific to our server architectures and workload demands, is crafted.
- Execution: Workloads are systematically migrated to the new servers with minimal impact.
Meticulous planning in this phase contributes to a smoother transition.
Validating Post-Migration Performance
To affirm the success of the migration, we rigorously evaluate the following post-migration:
- Functionality Tests: Ensuring all services are operational.
- Performance Checks: Benchmarking the system against predefined performance metrics.
The validation process confirms the migration aligns with our performance and availability goals.
Security Measures
In a migration checklist template, ensuring the integrity and confidentiality of data is paramount. We prioritize stringent security measures to mitigate risks and maintain compliance throughout the migration process.
Implementing Access Controls
We must establish robust access control mechanisms to protect sensitive data. This involves:
- Defining user roles: Clearly specifying permissions for each role to limit access on a need-to-know basis.
- Authentication protocols: Employing strong authentication methods such as multi-factor authentication to prevent unauthorized access.
Regular Security Assessments
To maintain a strong security posture, we conduct:
- Vulnerability scans: Regularly scanning our systems to detect and address potential vulnerabilities.
- Penetration testing: Simulating cyber attacks to evaluate the effectiveness of our security measures.
Compliance Audits
Our migration process is designed to comply with relevant regulations. We implement:
- Audit trails: Keeping detailed logs for all system accesses and data migrations to track adherence to compliance standards.
- Policy reviews: Periodically reviewing our policies against compliance frameworks to ensure ongoing conformance.
By embedding these practices into our migration checklist template, we strive to safeguard our data security against loss and bolster our defenses against diverse risks. Our assessments provide the insights necessary for continuous improvement and compliance adherence.
Monitoring and Optimization
In our migration checklist, it’s imperative to focus on maintaining system performance and controlling costs post-migration. We ensure our services remain scalable and available, while efficiently managing power and storage resources.
Performance Monitoring
We rigorously track system performance through real-time metrics to ensure that our service levels meet the agreed-upon standards. This includes monitoring CPU usage, memory consumption, and network bandwidth. We utilize tools to alert us to any anomalies that could indicate potential issues with scalability or availability.
- CPU Usage:
- Alert Threshold: > 90% for 5 minutes
- Baseline: 50% Average usage
- Memory Consumption:
- Alert Threshold: > 85% for 5 minutes
- Baseline: 60% Average usage
- Network Bandwidth:
- Alert Threshold: < 50 Mbps for 5 minutes
- Baseline: 150 Mbps Average usage
Cost Management
Managing costs effectively is non-negotiable for us. We implement detailed cost tracking and cost optimization strategies to get the best value from our resources. Regular reviews of our spending against our budget allow us to adjust as needed, ensuring that we’re not overprovisioning or underutilizing resources.
- Monthly Cost Reviews
- Compute: Align spending with usage patterns.
- Storage: Consolidate or expand based on data growth trends.
Continuous Improvement Planning
We are committed to continuous improvement and regularly revisit our strategies to confirm they still align with our business objectives. Our plans focus on scalability and availability to support growth, and include scheduled reviews of system power and storage needs to anticipate future requirements.
- Quarterly Strategy Sessions:
- Scalability checks to handle growth
- Availability assessments for peak times
Our checklist is a living document, continually refined to ensure peak performance and cost efficiency. By carefully monitoring and optimizing our systems, we uphold the quality of service our users expect.

